In today’s digitally-driven world, smartphones are indispensable to our daily lives, functioning as primary tools for communication, finance, and personal organization. However, a recent study conducted by researchers from Graz University of Technology has illuminated a troubling issue: many Android smartphones are vulnerable to well-documented cyberattacks, known as one-day exploits. As these devices are increasingly utilized for sensitive operations like online banking or handling governmental affairs, the implications of these vulnerabilities press heavily on both manufacturers and users alike.
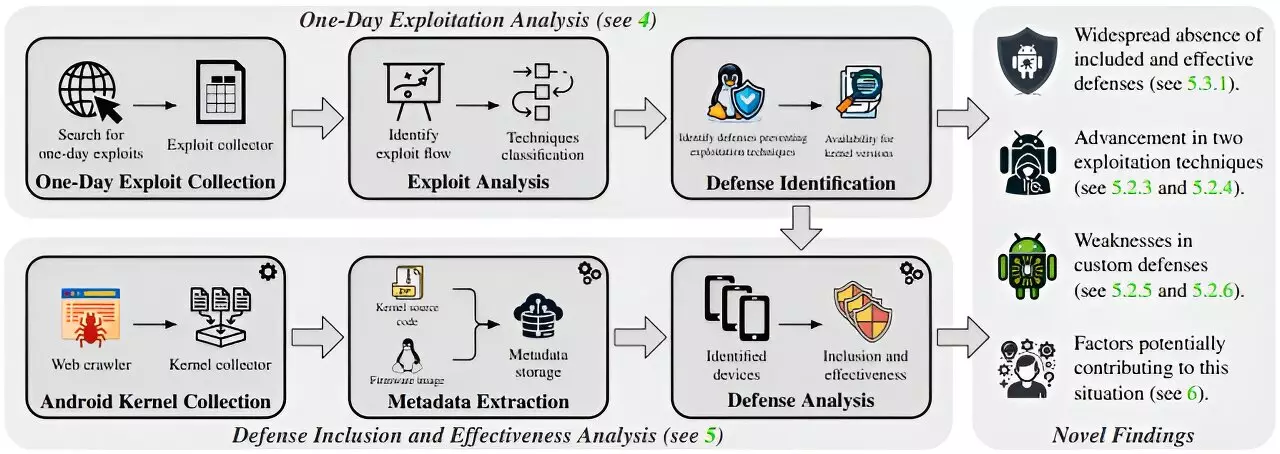
The analysis, presented at the Usenix Security Symposium, scrutinizes the Android kernels of 994 devices from ten major manufacturers, including Google, Samsung, and Huawei, which were released between 2018 and 2023. Despite the prevalence of robust protective mechanisms, it was startling to discover that the tested smartphones only managed to prevent attacks at varying success rates ranging from a mere 29% to 55%. In stark contrast, Google’s Generic Kernel Image (GKI) version 6.1 showcased a resolute 85% defense capability against attacks.
This troubling disparity reveals an alarming trend: the proprietary kernel versions—crafted by manufacturers—perform up to 4.6 times worse than Google’s own kernel. This research serves as a strong indictment of the security efforts undertaken by smartphone manufacturers, which seem, at best, insufficient, and at worst, negligent.
Delving deeper into the kernel versions used across these devices, researchers discovered that Android versions spanned from 9 to 14, with the kernels ranging from 3.10 to 6.1. An essential observation was that manufacturers utilizing older kernel versions demonstrated a significantly reduced level of security. Notably, even a 2014 kernel version like 3.1, when configured properly, could outperform 38% of the more contemporary yet poorly-configured kernels deployed by manufacturers.
This insight underscores the troubling reality that prior advancements in security protocols are not being effectively implemented or maintained in newer models. The fragmented landscape of Android devices means users grapple with inconsistent security postures, often unknowingly putting themselves at heightened risk.
Another critical finding of the research was the pronounced disparity in security between low-end and high-end models. The study indicated that low-end smartphones are approximately 24% more susceptible to attacks than their high-end counterparts. This vulnerability largely stems from the manufacturers’ tendency to disable security features in lower-end devices to reduce performance overhead.
Such choices reveal a disconcerting trade-off between performance and security, in which less affluent consumers face greater risks due to cost-cutting measures. This raises ethical questions about the responsibilities of manufacturers toward all consumers, regardless of their chosen device tier.
The study’s authors express hope that their findings will catalyze significant advancements in kernel security measures across the industry. They have shared their results with various manufacturers, prompting reactions ranging from acknowledgment to immediate action, as indicated by the release of patches from companies such as Motorola and Samsung.
Moreover, the researchers have urged Google to amend the Android Compatibility Definition Document (CDD), which serves as a framework guiding manufacturers on compliance and security. Heightened awareness from Google regarding these issues is promising; the company acknowledges the need to systematically bolster kernel security measures.
As smartphones evolve into increasingly critical instruments for our personal and professional lives, the challenge of ensuring their security grows ever more daunting. The findings from Graz University of Technology’s recent analysis lay bare the vulnerabilities that jeopardize millions of users and underscore the necessity for manufacturers to prioritize security over merely reducing costs.
Ultimately, addressing these vulnerabilities requires collective responsibility: manufacturers must implement more rigorous security protocols, while users must remain vigilant and informed. It is only through concerted efforts that we can hope to create a more secure digital ecosystem for all smartphone users.
Leave a Reply